Crypto security experts are the first responders of the blockchain world, tracing stolen millions across wallets, mixers and obscure bridges before the trail goes cold.
They operate in war rooms that form within minutes of a breach, using open-source intelligence, internal alert systems and private networks that span borders and languages.
When a major hack breaks, the crypto community turns to its pseudonymous detectives, whose social accounts are often the first to translate blockchain trails.

What began as hobbyists decoding suspicious transactions has evolved into a global web of digital sleuths who track the flow of stolen funds faster than most authorities. Their tools are open-source, their networks informal and their reputations built on credibility earned in public.
The night shift crypto detectives
The industry’s most recognized blockchain sleuth is ZachXBT. He’s built a reputation for precise onchain forensics cited by government bodies and investigations that have led to arrests.
Elsewhere in the ecosystem, an army of veteran researchers and self-taught hobbyists are doing similar work in the digital shadows. One of them is 0xSaiyanGod, a security researcher who built a bot to detect malicious sites and spent years tracing drainer groups.
“I introduce myself as a legendary Super Saiyan, Prince of all Saiyans — or other crazy nicknames — but I’m 0xSaiyanGod,” he tells Magazine. “Most people just call me Saiyan.”
Saiyan works under a pseudonym but he repeatedly emphasized the importance of sharing credit with the teams he works with. He requested that his interview with Magazine be conducted with the video turned off citing security concerns.
Like many of his peers, Saiyan has a life outside the screen. He works a regular job by day and hunts crypto scams by night under his digital alias.
“I still have a nine-to-five. Then I come home, open Telegram, check the reports and start tracing wallets. It’s the same rhythm every night,” he says.
He began as a bug bounty hunter in the Web2 scene and brought that skillset into crypto security in 2022. Early on, he tracked SIM-swapping phishing campaigns and the social engineering tactics behind wallet drainer operations with groups such as Wallet Guard and the security collective BlockMage.
One of the key cases he worked on was the Blur browser extension scam with researcher NFT_Dreww — where Inferno Drainer tricked victims into installing a malicious add-on.
Saiyan’s first encounter with drainer activity was during the period when Monkey Drainer–style phishing kits were spreading across Telegram. Saiyan mapped the infrastructure behind such campaigns, including reused phishing templates, shared hosting setups and recurring wallet-chaining patterns. His work has since expanded to successor clusters associated with Inferno Drainer, where small code overlaps helped researchers flag new phishing domains.
To scale detection, he built Doom Bot, a Discord-based phishing and drainer detection bot that flagged suspicious links and forwarded them into private channels. Doom Bot and its peers were early movers in the space before larger teams such as SEAL took on that function.
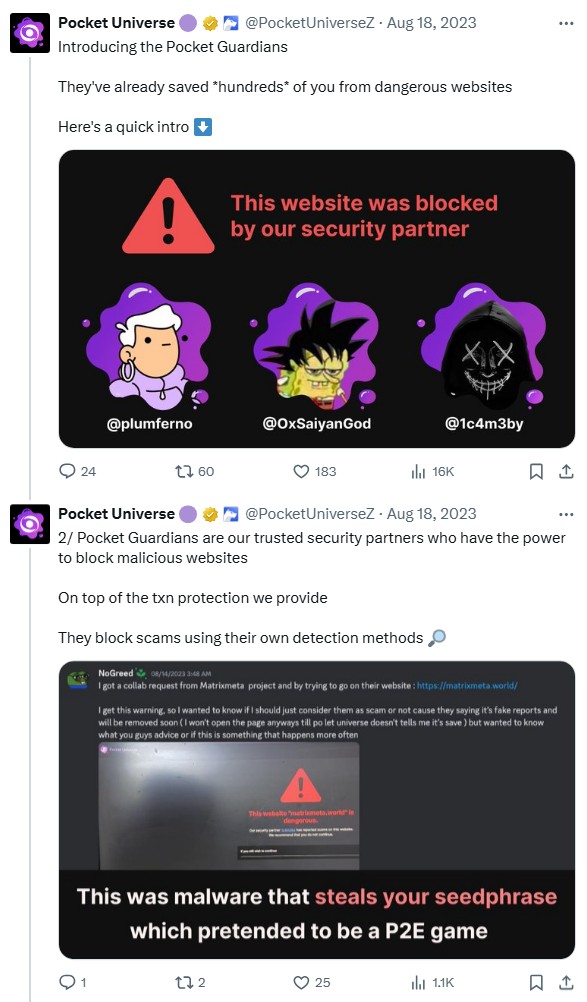
“The intel provided to those teams at that time was definitely helpful,” Saiyan says.
“I can reference one tool of my buddy that was — maybe still — doing the same and reporting to Pocket Universe. Between us, we could catch most links and provide the intel to teams.”
The tracing work that follows is still manual. Saiyan took part in identifying and flagging wallets tied to North Korean–linked activity during the $1.5 billion Bybit incident, publicly marking addresses on Etherscan. He uses tooling such as blockchain explorers, Arkham, MetaSleuth and Breadcrumbs. High-end forensics platforms like Chainalysis are typically reserved for law enforcement and institutional teams.
The human side of crypto investigations
While most crypto detectives use pseudonyms, Heiner Garcia does not. A former security analyst for Colombia’s Ministry of Defense, he spent years in human intelligence operations tied to criminal networks before joining Telefónica’s security division.
“I’ve dealt with real risk,” he says. “Narcos, corrupt politicians, soldiers, police — the kind of work where you actually hide because someone might kill you.”
That experience shaped how he views the online threat landscape.
“The real danger isn’t here, behind a computer,” he says. “If I get doxxed online, fine. But if I get doxxed out there, I might get killed.”
His investigations rely heavily on human intelligence principles — reading context, studying behavior and blending into digital environments.
“Everything is context,” he says. “If you want to understand a target, you have to understand what’s around them — what they like, how they connect, the tools they use.”
⚡️ INSIGHT: A North Korean crypto spy pretending to be a Japanese crypto dev walked into a fake job interview set up by security researcher Heiner Garcia. Cointelegraph was invited to attend undercover. By the end, he rage-quit and left behind a trail of breadcrumbs. pic.twitter.com/pZ6F11ElfL
— Cointelegraph (@Cointelegraph) May 7, 2025
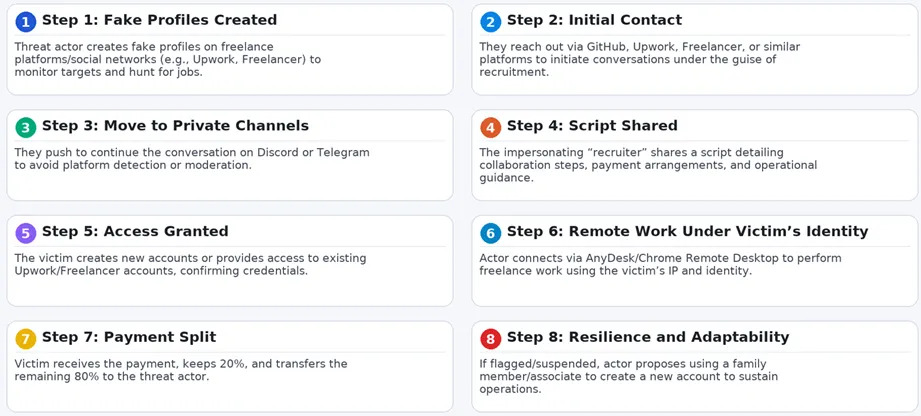
Garcia builds fake profiles that mirror the developers or hackers he studies. He gets so close to his targets that some of them even follow his fake profiles.
Within the crypto security community, Garcia has built a reputation for profiling and even interacting with suspected North Korean IT workers. “If I see five different profiles using the same avatar, same code patterns and the same repositories, I know it’s coordinated,” he says.
In one case, he traced a cluster of North Korean developers by posing as a collaborator on open-source projects.
“They thought I was one of them,” he says. “I saw how they recruit others, how they communicate, what tools they use to move money. It’s human intelligence, not cyber forensics.”
Garcia’s approach, which blends OSINT with HUMINT, reveals behavioral patterns that automated tools often miss.
“If you only look at IPs and malware, you’re chasing ghosts,” he says. “But if you understand the people — their motives [and] their routines — you start seeing the structure behind the operations.”
Inside a crypto incident response war room
When a hack breaks out, intelligence work shifts from routine monitoring to crisis response. Across the blockchain security world, the first move is to open a channel for collaboration
“The moment an incident starts, we open a war room,” Cos, founder of security company SlowMist, tells Magazine through a Mandarin interpreter. “The goal is to trace, contain and alert as fast as possible.”
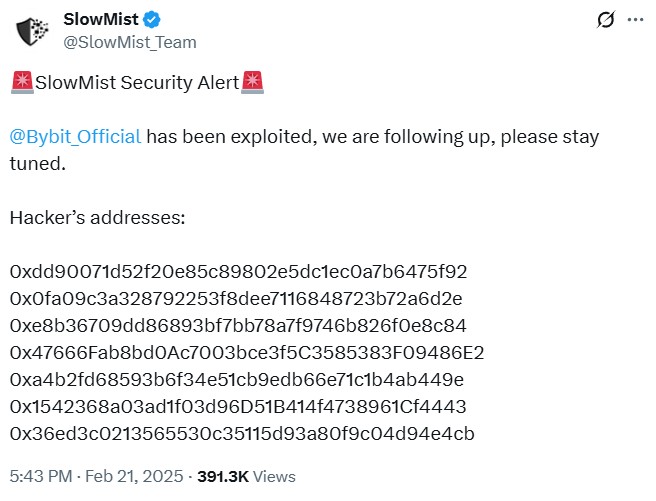
It starts off as an invite-only channel with trusted responders. As the incident develops, more parties — such as exchanges, partners and victims — join the war room. Even representatives from law enforcement agencies enter the chat.
Communication is tightly managed. Victims are often asked to send their public statements or screenshots to the group before posting them, so sensitive details don’t leak mid-operation.
Law enforcement usually joins after the initial tracing work is underway.
“We need to move first,” Cos explains. “Law enforcement moves slower. They need evidence; we need speed.”
Behind the scenes, SlowMist’s internal tooling supports all of this. MistTrack is used for wallet tracing and transaction visualization, while MistEye scans for malicious domains, phishing infrastructure, and contract-level exploits.
Crypto security needs reinforcements
The broader crypto security community is still understaffed as hacks get larger and laundering paths grow more complex, while the number of trained defenders has not kept pace. Many major incidents are still first flagged by independent volunteers.
“There are always new attacks. Every week something happens. There are not enough people in security, not enough analysts and not enough responders. We need more people who can actually do the work,” Cos says.
Saiyan, who works security on top of his full-time job, says those interested in joining the field need curiosity more than credentials.
“You don’t need to be an expert from day one, you just need to look closer than everyone else,” he says. “Trace every line and ask why something moved the way it did.”
Meanwhile, Garcia advises future crypto sleuths to find a niche.
“You can’t be good at everything. Find the niche you love, study the context around it and do something outstanding,” Garcia says.
Paths into the field vary. Some like Saiyan come from bug bounty circles and self-taught scripting. Others, like Garcia, arrive with military or intelligence backgrounds. Companies like SlowMist combine structured response frameworks with open-source instincts. What unites them is the impulse to protect an industry worth $3.5 trillion.
For Cos, the core challenge is ethical. His X handle, @evilcos, serves as a reminder of exactly where he stands, because in this field, the skills used to defend systems can just as easily be used to exploit them.
“You have to decide what kind of person you want to be,” he says. “You see a lot of money in this work and the line between good and bad can get blurry. Don’t be evil.”

Yohan Yun
Hamster Kombat tappers evolve with Swipe-to-Earn + Axie Pals Tamagotchis: Web3 Gamer
Hamster Kombat is “lighthearted and fun” but tap-to-earn gameplay is evolving; gamers playing 80-hrs a week to win a $100K prize: Web3 Gamer.
Read moreGoldman Sachs buying crypto firms, FTX news, 3AC and Celsius updates: Hodler’s Digest Dec. 4-10
FTX will be the subject of a U.S. Senate hearing, authorities take HashFlare founders into custody and New York finalizes its PoW ban.
Read moreWeb3 games shuttered, Axie Infinity founder warns more will ‘die’: Web3 Gamer


